Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Last updated 18 junho 2024

A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

Comparison of different approaches for direct coupling of solid-phase microextraction to mass spectrometry for drugs of abuse analysis in plasma - ScienceDirect

Microsoft Defender Attack Surface Reduction recommendations

Cabotegravir for the prevention of HIV-1 in women: results from HPTN 084, a phase 3, randomised clinical trial - The Lancet

101 Landing Page Optimization Tips & Ideas
:max_bytes(150000):strip_icc()/ESOP_Final_4196964-2e25b96d22ce437497a38754c6c866ff.jpg)
Employee Stock Ownership Plan (ESOP): What It Is, How It Works, Advantages

The UTI Emergency Kit
10 Common Web Security Vulnerabilities
Learn how to add Input Validation to a REST API with NestJS and Prisma

Judicial Ethics Becomes a Political Football - Non Profit News

Met Council may add Metro Transit security, enforce code of conduct - Minneapolis / St. Paul Business Journal

What is Remote Code Execution (RCE) Vulnerability❓
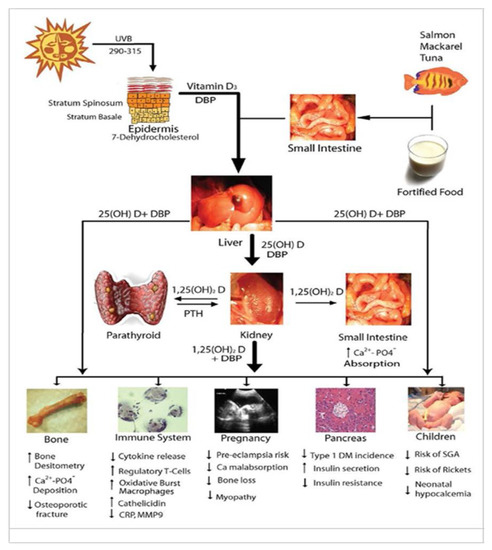
Nutrients, Free Full-Text
Recomendado para você
-
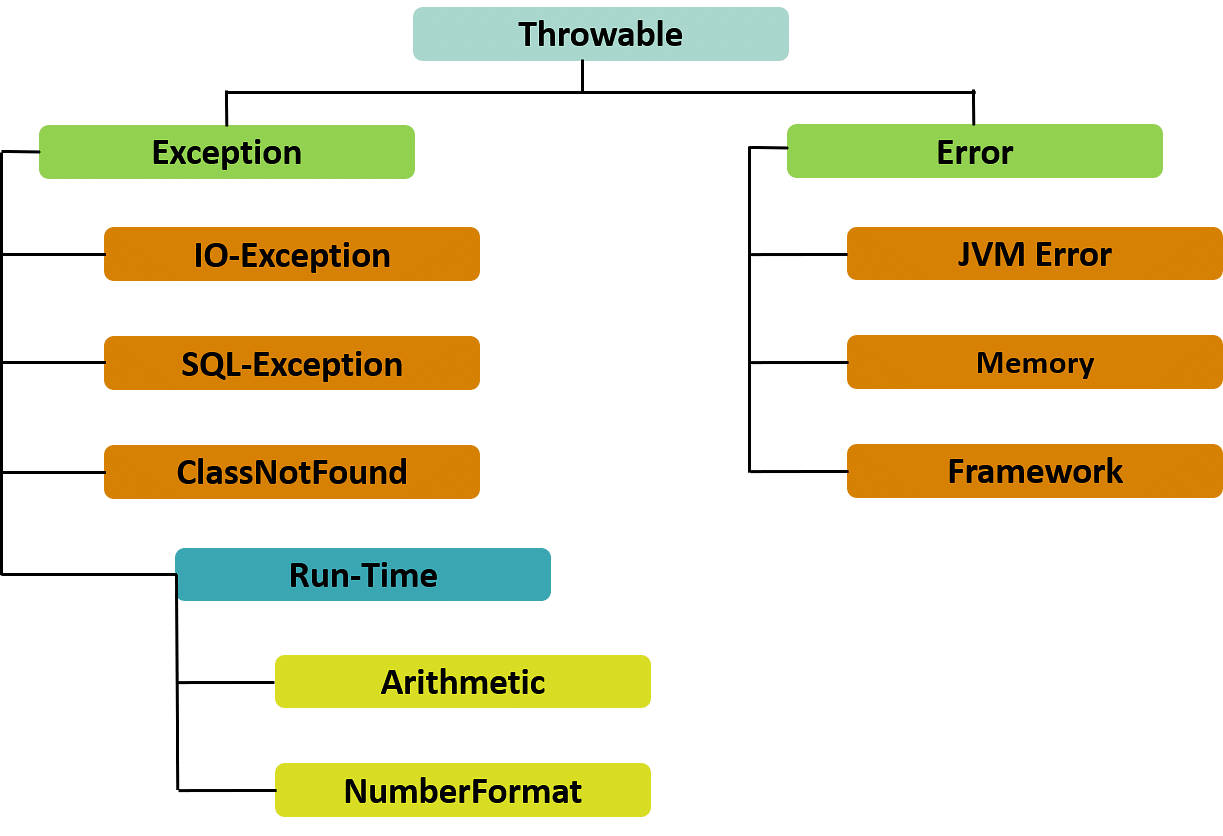 What is Exception Handling in Java?18 junho 2024
What is Exception Handling in Java?18 junho 2024 -
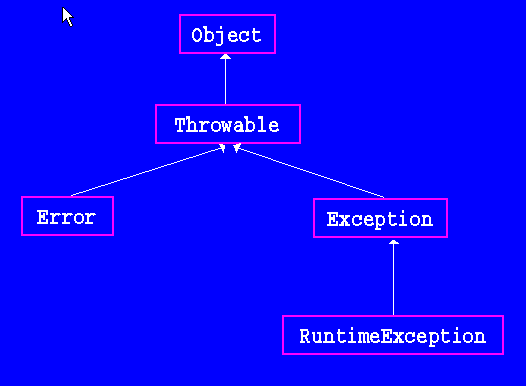 Exceptions and Inheritance18 junho 2024
Exceptions and Inheritance18 junho 2024 -
 Auditing Exceptions and How They Might Impact Your SOC Reports18 junho 2024
Auditing Exceptions and How They Might Impact Your SOC Reports18 junho 2024 -
 The Exceptions, Book by Kate Zernike, Official Publisher Page18 junho 2024
The Exceptions, Book by Kate Zernike, Official Publisher Page18 junho 2024 -
 Implement Custom Exceptions in Java: Why, When and How18 junho 2024
Implement Custom Exceptions in Java: Why, When and How18 junho 2024 -
 Additional VP Initials for Exceptions18 junho 2024
Additional VP Initials for Exceptions18 junho 2024 -
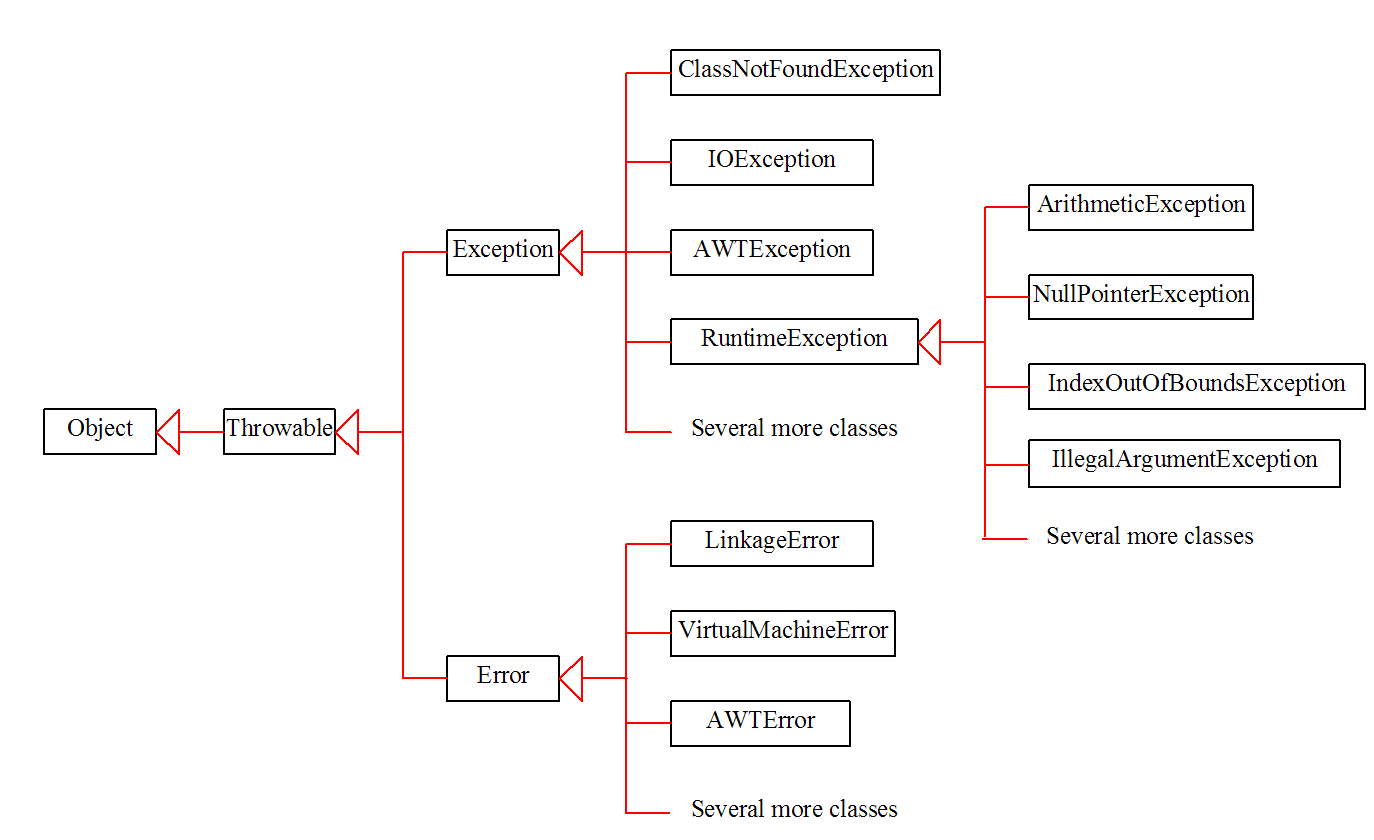 CIS 35A: Introduction to Java Programming18 junho 2024
CIS 35A: Introduction to Java Programming18 junho 2024 -
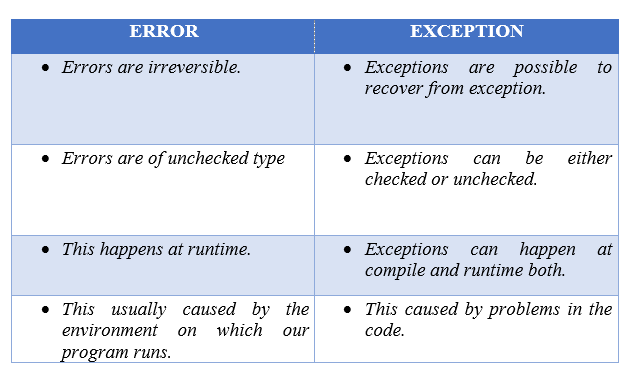 Exception Handling in Java.. Hello Guys, This article will include…, by Prithvi Dev, Javarevisited18 junho 2024
Exception Handling in Java.. Hello Guys, This article will include…, by Prithvi Dev, Javarevisited18 junho 2024 -
 Exceptions Stock Photos, Royalty Free Exceptions Images18 junho 2024
Exceptions Stock Photos, Royalty Free Exceptions Images18 junho 2024 -
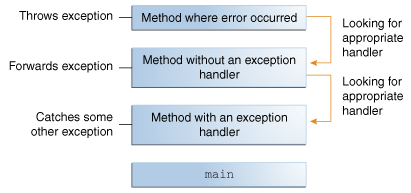 What Is an Exception? (The Java™ Tutorials > Essential Java Classes > Exceptions)18 junho 2024
What Is an Exception? (The Java™ Tutorials > Essential Java Classes > Exceptions)18 junho 2024
você pode gostar
-
 DEATH'S GAMBIT: AFTERLIFE Review: A Fair Challenge In A Confusing Map — GameTyrant18 junho 2024
DEATH'S GAMBIT: AFTERLIFE Review: A Fair Challenge In A Confusing Map — GameTyrant18 junho 2024 -
 Photos at Costco - Puyallup, WA18 junho 2024
Photos at Costco - Puyallup, WA18 junho 2024 -
 Light Novel - KirukaXV - Wattpad18 junho 2024
Light Novel - KirukaXV - Wattpad18 junho 2024 -
 Final da Europa League hoje: que horas começa e onde assistir?18 junho 2024
Final da Europa League hoje: que horas começa e onde assistir?18 junho 2024 -
Pawns.app MOD APK v1.0.2 (Unlocked) - Jojoy18 junho 2024
-
 Blusa Moana Laranja ManuManu Brand Moda Feminina18 junho 2024
Blusa Moana Laranja ManuManu Brand Moda Feminina18 junho 2024 -
 Minecraft SCP foundation: building SCP-007 pt 118 junho 2024
Minecraft SCP foundation: building SCP-007 pt 118 junho 2024 -
 Boruto: Primeira parte do animê “chega ao fim” este mês18 junho 2024
Boruto: Primeira parte do animê “chega ao fim” este mês18 junho 2024 -
 Agenda da Copa: veja horários e onde assistir aos jogos desta segunda-feira18 junho 2024
Agenda da Copa: veja horários e onde assistir aos jogos desta segunda-feira18 junho 2024 -
 Call of Duty: Modern Warfare 2 Season 2 adds just two new 6v618 junho 2024
Call of Duty: Modern Warfare 2 Season 2 adds just two new 6v618 junho 2024